What is Threat Intelligence?
Gain the proactive edge in defense against threats with Threat Intelligence. Explore its definition, significance, variations, and lifecycle, and delve into the realm of Advanced Threat Intelligence.
What is Threat Intelligence?
Threat intelligence is the process of gathering, analyzing, and disseminating information about existing and potential threats. This information can be used to:
- Identify and evaluate threats: Organizations can leverage threat intelligence to pinpoint possible threats, ranging from cyberattacks to malware and physical security risks. Additionally, it aids in evaluating the seriousness of these threats and understanding their potential impact.
- Protect against threats: By utilizing threat intelligence, organizations can formulate and execute security measures to shield themselves from potential threats. It facilitates proactive actions and the development of effective defense strategies. For instance, organizations can employ threat intelligence to detect and rectify system vulnerabilities, preventing exploitation.
- In-depth insights into the threat landscape: The information generated by threat intelligence tools offers organizations a comprehensive understanding of the threat landscape, specifically tailored to their business and industry context. This can be used to help prioritize risk in their environment.
To leverage threat intelligence, cybersecurity teams often take one of three paths:
- Manually comparing their findings against public threat intel feeds, like CISA KEV or NIST
- Incorporating Advanced Threat Intelligence from a vendor or provider
- Compiling and customizing their own threat intelligence
By carefully selecting the most suitable approach, organizations can enhance their security posture and better defend against emerging threats.
Why is Threat Intelligence Important?
In the constantly evolving digital landscape, threats come from many directions. In 2023, a diverse array of attacks, ranging from ransomware to software supply chain compromises, underscored the dynamic nature of cyber threats. The ongoing race between hackers and defenders to outpace each other further intensifies the cybersecurity challenge.
Cloud computing and artificial intelligence have expanded the attack surfaces that must be safeguarded, presenting unprecedented challenges. This is precisely where threat intelligence proves invaluable. It empowers security teams to proactively prepare for, prevent, and swiftly respond to threats. By doing so, threat intelligence not only safeguards organizations from potentially crippling cyber attacks but also contributes to substantial cost savings, potentially in the millions.
Business stakeholders can make judicious investments and informed security decisions by leveraging the insights provided by threat intelligence. Cyber threat intelligence equips security professionals with the knowledge of threat indicators, tactics, techniques, and procedures, enabling them to take effective actions against cyber attacks.
Threat Intelligence Lifecycle
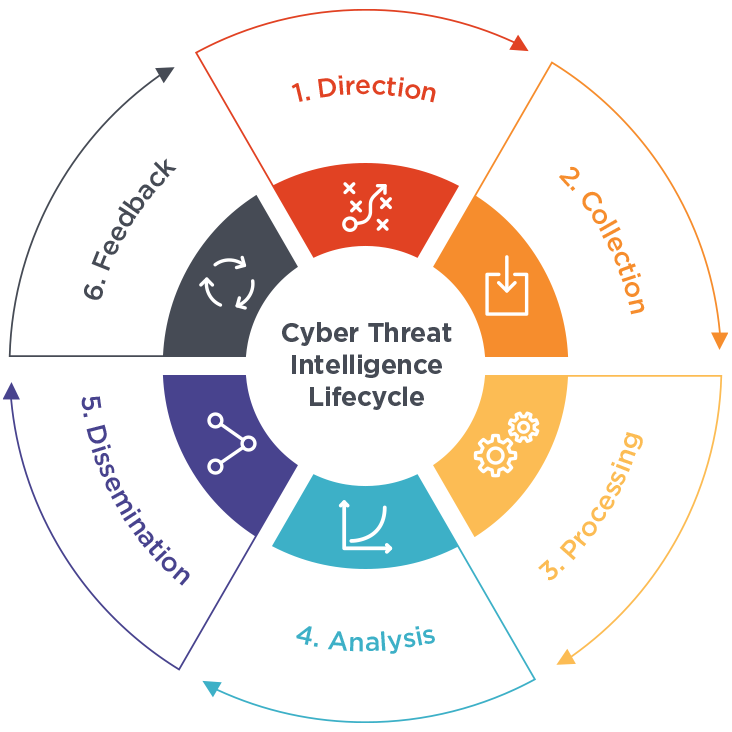
The threat intelligence lifecycle is the structured process by which organizations gather, process, analyze, and use threat intelligence. It’s a continuous and iterative cycle that helps security teams proactively identify, understand, and respond to threats before they can cause harm.
Here are the six key phases of the threat intelligence lifecycle:
1. Direction
It is the most crucial phase to guide the entire threat intelligence program. This phase sets the foundation by defining the goals, objectives, and scope of the threat intelligence program. The stakeholders need to answer the following questions as it helps set focus on the Collection and Analysis phase.
- What are the organization’s security priorities?
- What types of threats are most concerning?
- What actions need to be taken to prevent future attacks?
2. Collection
In this phase, the security professionals collect data that can help fulfill the requirements set in Phase 1. The quality and quantity of data are both crucial to avoid false positives and miss any events. Data can be collected from various sources, both internal and external. Some of the data sources include security and traffic logs, incident reports, security forums, social media, interviews with subject matter experts, and open-source news sites.
3. Processing
The raw data collected needs to be cleaned, normalized, and formatted for analysis. This may involve removing duplicate information and false positives, enriching data with context, fact-checking, and lastly converting it into a usable format.
4. Analysis
In this phase, the raw usable data is converted into actual threat intelligence. The analysts decipher the data and verify the trend and pattern to answer the stakeholder’s questions from the Requirement phase and also make valuable recommendations.
5. Dissemination
The intelligence and recommendations need to be communicated in the form of reports to the right people in the organization who can take action. This may involve security analysts, incident responders, IT administrators, and even executives. The format and level of detail need to be tailored to the recipient’s needs to avoid confusion during decision-making.
6. Feedback
The final phase of the threat intelligence lifecycle ensures the effectiveness of the threat intelligence program. Users who receive the reports in the last phase provide feedback on their relevance, accuracy, and timeliness. This feedback is used to improve the collection, analysis, and dissemination of intelligence in future cycles.
Note: The tasks carried out during these phases may vary among different organizations. Nevertheless, the fundamental essence remains consistent.
With the threat intelligence lifecycle, organizations can maximize the value of their threat intelligence and gain a proactive advantage in cybersecurity.
Types of Threat Intelligence

Cyber threat intelligence is split into three main categories based on the intelligence produced after the threat intelligence lifecycle. Each category serves a different purpose.
Strategic Threat Intelligence
Focus: Big picture analysis of the threat landscape, identifying emerging threats, motivations of threat actors, and overall risk to the organization.
Strategic threat intelligence provides a high-level overview of the threat landscape, including emerging threats, the motivations of threat actors, and the overall risk to an organization. It is designed to inform decision-making by senior management and executives. This type of threat intelligence helps with long-term security strategies, resource allocation, and investment decisions.
Tactical Threat Intelligence
Focus: Highly granular details about individual threats, including attack steps, specific vulnerabilities exploited, and attacker communication patterns.
Tactical threat intelligence provides very specific information about individual threats, such as the steps involved in an attack and the vulnerabilities being exploited. It is used by security analysts to take immediate action to mitigate threats. This type of threat intelligence facilitates rapid containment, forensic analysis, and targeted defense measures. It identifies simple indicators of compromise (IOCs) such as bad IP addresses, known malicious domain names, unusual traffic, and file hashes related to known ransomware and malware attacks.
Operational Threat Intelligence
Focus: Actionable information about specific threats, such as indicators of compromise (IOCs), malware signatures, and active campaigns.
Operational threat intelligence provides more detailed information about threats, such as nature, motive, timing, and process. This information is used by security analysts to detect and respond to threats in real time. It enables proactive threat detection, timely incident response, and mitigation actions.
| Feature | Strategic | Operational | Tactical |
|---|---|---|---|
| Focus | Threat landscape trends | Specific threats & campaigns | Individual threat details |
| Audience | Executives | Security analysts | Incident responders, threat hunters |
| Information level | High-level overview | Actionable data | Highly granular details |
| Value | Long-term strategic planning | Threat detection & response | Deep understanding & targeted mitigation |
| Limitations | Less actionable | Potential for false positives | Requires technical expertise |
Advanced Threat Intelligence (ATI)
Advanced threat intelligence (ATI) goes beyond basic threat data to provide deeper insights and context into emerging threats, threat actors, and their attack methods. It aims to give organizations a more comprehensive understanding of the ever-evolving threat landscape.
ATI is a continuous process that involves collecting, analyzing, and disseminating threat intelligence on an ongoing basis. Additionally, it focuses on understanding the motivations, capabilities, and tactics of threat actors, rather than just the individual threats themselves.
Benefits of Using Advanced Threat Intelligence
ATI can be seen as an insurance policy against potential cyberattacks, ultimately saving organizations significant costs and reputation damage.
- Early threat detection: ATI provides real-time insights into emerging threats and tactics, allowing organizations to identify potential attacks before they occur. This proactive approach significantly reduces the risk of successful breaches and data loss.
- Informed decision-making: With detailed threat actor profiles, attack methods, and vulnerability information, security teams can make data-driven decisions about resource allocation, security investments, and response strategies. This leads to more targeted and effective security measures.
- Reduced risk of breaches: By understanding the specific threats targeting their industry and infrastructure, organizations can prioritize vulnerabilities and implement targeted defensive measures, significantly reducing the attack surface and the likelihood of successful exploitation.
- Faster incident response: ATI helps teams identify and categorize incidents quickly, understand their scope and potential impact, and implement appropriate mitigation strategies faster. This minimizes damage and downtime.
- Improved resource allocation: With a clear understanding of the most critical threats, organizations can prioritize security resources, developer’s time and efforts, and investments towards the areas with the highest risk, ensuring efficiency and maximizing the impact of security efforts.
- Proactive threat hunting: ATI empowers security teams to proactively search for hidden threats within their network, uncovering potential compromises before they escalate into major incidents.
- Compliance and regulatory requirements: Many industries have regulations requiring organizations to implement specific security measures and threat intelligence practices. ATI helps organizations meet these requirements and demonstrate their commitment to cybersecurity.
Which Type of Threat Intel is Right for Me?
There exist multiple methods for generating threat intelligence. You can choose to utilize publicly available feeds such as CISA KEV, follow the threat intelligence lifecycle to create custom threat intelligence or employ advanced threat intelligence services from vendors.
Each strategy has its advantages and disadvantages. The most suitable approach depends on factors such as the size of your organization, resource availability, specific security requirements, and tolerance for risk.
| Description | Pros | Cons |
|---|---|---|
| Public Feeds | Easy access and no maintenance costs.Useful for understanding broader threat trends. | Often lags behind real-time threats, lacking specific details.May not be tailored to your unique vulnerabilities. |
| Custom Threat Intelligence | Highly tailored to your organization’s needs and risk profile.Provides deeper insights into potential attack scenarios. | Requires significant effort, expertise, and resource investment.Building and maintaining internal databases can be complex. |
| Advanced Threat Intelligence | Offers precise, real-time insights into emerging threats and vulnerabilities.Can significantly reduce the time and expertise required for intelligence gathering. | Involves subscription costs, adding to security expenses.Limited control over data sources and analysis methodologies. |
Effective threat intelligence requires ongoing evaluation and adaptation based on your evolving security posture and the threat landscape.
Advanced threat intelligence solutions enhance threat intel databases by incorporating predictive measures such as EPSS, dark web monitoring, social trend analysis, and threat actor intelligence. This comprehensive approach ensures a more precise and current evaluation of threats. However, some organizations may struggle with managing the vast amounts of data involved, requiring validation and extraction of actionable insights, which can be both intricate and time-consuming.
Moreover, there is a challenge in effectively correlating threat intelligence data with vulnerabilities, further complicated by the sheer volume of information to be handled. Security teams often find themselves navigating between multiple tools for threat intelligence and vulnerability management, dedicating substantial time and effort to prioritize vulnerabilities based on threat intelligence scores.
To address these challenges, organizations require a unified platform that integrates vulnerability and threat intelligence data seamlessly.
ArmorCode’s Advanced Threat Intelligence
Advanced cyber threat intelligence can help organizations build defense mechanisms against cyber attacks. However, with so many threats, it becomes important to prioritize them based on criticality, trends, and exploits. ArmorCode’s Advanced Threat Intelligence, also known as AATI, can help with it.
ArmorCode automatically ingests and applies relevant data to calculate the risk of vulnerabilities and prioritize remediation efforts.
AATI goes beyond the public domain sources of NIST NVD and CISA KEV to provide more accurate and up-to-date risk scoring, ensuring that the most critical and impactful vulnerabilities are addressed first. It takes into account hacker discussion, pentester framework, proof of concepts, ransomware association, exploits, threat actor association, social trending, and attack signatures.
By incorporating AATI scores into risk scoring, security teams can make more informed decisions about which threat to prioritize over others. Get more accurate scoring and efficient prioritization with AATI.
3 Mandatory Steps to Mature your AppSec Program Today
Read this whitepaper to discover how to mature beyond scanning and burn down your critical security debt by >80%.


