What is Penetration Testing (Pentesting)?
Explore how penetration testing helps safeguard your systems by identifying vulnerabilities before cybercriminals can exploit them.
In an age where data breaches and cyberattacks are becoming alarmingly common, ensuring the security of your systems, applications, and networks has never been more critical. Organizations today face a constant barrage of sophisticated threats that can exploit vulnerabilities in their defenses. To stay ahead of cybercriminals, businesses must proactively test their security measures. This is where penetration testing, also known as, pentesting, comes in.
Pentesting is a vital practice in cybersecurity that allows organizations to identify and address security weaknesses before they can be exploited by malicious actors.
What is Pentesting?
Penetration testing simulates real-world cyberattacks to uncover weaknesses before malicious hackers can exploit them. By simulating real-world attacks, pentesting helps you see your system through the eyes of a hacker, exposing vulnerabilities that might otherwise go unnoticed. It allows organizations to fix the weaknesses and vulnerabilities before they turn into security breaches, thus reducing the risk of data theft, financial loss, and reputational damage.
Pentesting is often referred to as ethical hacking as it involves authorized individuals attempting to breach a system’s security controls. Unlike malicious hackers, ethical hackers work with the organization’s permission to identify vulnerabilities and weaknesses.
In a world where cyber threats continue to rise, penetration testing plays an essential role in protecting businesses and their customers.
Why is Penetration Testing Important?
According to IBM, the global average cost of a data breach in 2024 is $4.88 million. Pentesting allows organizations to take a proactive approach to breach prevention. Beyond this, there are five additional reasons why pentesting is crucial for businesses:
- High-Fidelity, High True-Positive Results:
Penetration testing provides a highly accurate assessment of an organization’s security posture by simulating real-world attacks. This high-fidelity aspect is critical because it ensures that security teams focus on genuine vulnerabilities that pose real risks, instead of chasing down false alarms. - Identifying Business Logic Flaws:
Certain complex vulnerabilities, such as business logic flaws can only be identified through manual pentesting, where testers use their expertise to assess how systems function under specific scenarios. Pentesting is essential for finding these deeper, more elusive vulnerabilities. - Offensive Security Perspective:
Penetration tests provide an offensive security viewpoint, simulating the mindset of a malicious attacker. This complements an organization’s defensive strategies by anticipating potential attack vectors that may not be visible through standard defense mechanisms. This offensive approach augments the capabilities of defensive teams and tools, helping organizations predict and preempt cyberattacks. - Regulatory Compliance:
Many industries require businesses to perform regular penetration tests to meet regulatory standards such as GDPR, HIPAA, and PCI-DSS. Pentests ensure that organizations comply with these standards, avoiding penalties and helping secure sensitive customer data. - Maintaining Trust:
Pentesting helps organizations maintain trust by safeguarding customer data and ensuring business continuity. In today’s digital environment, demonstrating a proactive security stance helps reassure clients and stakeholders that their information is being protected.
Pros and Cons of Penetration Testing
Pros:
- Advanced detection of security weaknesses and vulnerabilities: Pentests reveal vulnerabilities before attackers can exploit them, helping businesses strengthen their defenses.
- Improved security posture: Regular testing ensures continual improvement of security measures against evolving threats.
- Stakeholder assurance: Demonstrates commitment to security and compliance, building trust with clients and regulatory bodies.
Cons:
- High costs: Conducting thorough penetration testing can be expensive, especially for large organizations with complex systems.
- Potential disruptions: Testing can potentially disrupt normal operations, especially if it involves the production environment.
- False sense of security: A poorly executed pentest can miss key vulnerabilities, leaving the organization exposed.
Types of Pentesting
Black Box Testing
Black box testing is a method in which the penetration tester has no prior knowledge of the target system. The tester operates as an external attacker would, attempting to breach the system by probing its defenses without any internal access or information. This type of testing is valuable because it simulates a real-world attack scenario, where the hacker is working blind and must rely on publicly available information to exploit vulnerabilities. Black box testing can reveal how an organization’s external-facing systems, such as web applications and networks, stand up to potential cyberattacks.
However, the lack of insider knowledge also limits the scope of black box testing. It may miss deeper vulnerabilities within internal systems that aren’t easily accessible from the outside. Because the tester doesn’t have full access to the system’s architecture or source code, they may fail to identify complex issues like business logic flaws or deeper security holes. While black box testing is useful for assessing the strength of external defenses, it is often complemented by other forms of testing to provide a more comprehensive security assessment.
White Box Testing
In contrast to black box testing, white box testing provides the penetration tester with full access to the internal workings of the system, including architecture diagrams, source code, and network configurations. This method allows the tester to analyze the system from the inside out, gaining a deep understanding of how the system operates. White box testing is particularly effective in uncovering vulnerabilities that may be hidden deep within the codebase or in the system’s configuration. It helps testers identify complex flaws such as logic errors, authentication issues, and security misconfigurations.
Because of the tester’s full access, white box testing is thorough and can provide highly detailed insights into the security posture of an organization. However, this approach may not fully mimic a real-world external attack, as it assumes that the attacker has complete knowledge of the system—something that is rarely the case. White box testing is often used alongside other methods, like black box testing, to strike a balance between thorough internal assessment and realistic external threat scenarios.
Gray Box Testing
Gray box testing is a hybrid approach, where the tester has partial knowledge of the system—more than in black box testing but less than in white box testing. The tester might be given some credentials or limited access to parts of the system but not full transparency. This method simulates an insider threat or an attacker who has gained limited access through a breach or compromised account. Gray box testing is particularly useful for testing applications or systems from the perspective of a user with some, but not full, privileges.
This approach allows the tester to explore vulnerabilities that may arise from incomplete or improper access controls, role-based permissions, or internal misuse of resources. It provides a more realistic simulation of potential insider threats or attacks that come from users within the organization. Gray box testing strikes a balance between the depth of white box testing and the external perspective of black box testing, making it an effective way to assess both internal and external security threats.
Industry-Specific Tests
Penetration testing can be tailored to specific industries or environments, depending on the unique risks and challenges they face. For example, network penetration testing focuses on identifying vulnerabilities in an organization’s network infrastructure, including firewalls, routers, and switches. This type of test is particularly critical for industries such as financial services and healthcare, where network security is paramount. Application penetration testing, on the other hand, focuses on testing web and mobile applications for vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws. Industries that rely heavily on customer-facing applications, like e-commerce, prioritize this type of testing.
Similarly, cloud penetration testing addresses the unique security challenges associated with cloud environments, which are becoming increasingly common across industries. These tests focus on ensuring that cloud configurations, APIs, and storage services are secure and not vulnerable to attack.
Each industry or environment may have its own specific requirements and vulnerabilities, and industry-specific testing ensures that an organization’s particular needs are met. Tailored tests help address compliance requirements and specific security threats that are unique to different sectors, whether it’s healthcare, retail, or government.
Manual vs. Automated Pentesting
Both manual and automated pentesting approaches offer distinct advantages and drawbacks:
Manual Pentesting:
- Pros: Human testers bring creativity and problem-solving abilities that automated tools can’t replicate. This approach uncovers more complex vulnerabilities, such as logic flaws or subtle design weaknesses.
- Cons: It is time-consuming, resource-intensive, and more expensive, especially for larger or more complex systems.
Automated Pentesting:
- Pros: Automated tools are fast, scalable, and can be run frequently to identify common vulnerabilities. They are particularly useful for repeatable testing tasks.
- Cons: Automated testing can miss nuanced vulnerabilities that require human intuition to detect. It is also limited in its ability to assess business logic flaws.
While automated tools can accelerate the scanning process, manual testing often provides a more in-depth analysis and can uncover vulnerabilities that automated tools might miss. A combination of both manual and automated techniques is often used in effective penetration testing engagements.
Phases of Pentesting
Pen testers typically follow these seven steps:
- Scoping & Scheduling
Before any pentest begins, it is essential to define the scope and objectives of the test. This phase involves detailed discussions between the organization and the penetration testing team to determine what assets will be tested, such as networks, applications, or specific systems. The scoping process also sets the boundaries of the test, ensuring that critical systems are either included or excluded as per the organization’s needs. Additionally, the schedule is agreed upon to minimize disruption to business operations. Proper scoping ensures that the test remains focused, efficient, and aligned with the organization’s security goals, while scheduling helps avoid conflicts or unnecessary downtime during business hours. - Planning & Reconnaissance
Once the scope is set, the planning and reconnaissance phase begins. Testers gather as much information as possible about the target system, using both passive and active methods to understand its architecture, vulnerabilities, and exposure points. This information could include details like domain names, IP addresses, software versions, and network topology. The reconnaissance phase is critical because it lays the groundwork for the rest of the test, allowing the testers to focus their efforts on specific areas that may be vulnerable. Effective reconnaissance helps testers identify entry points and potential weaknesses, which will later be explored in more depth. - Scanning
After gathering initial information, testers move on to scanning, where they use automated tools to identify vulnerabilities in the system. These scans help pinpoint specific weaknesses, such as open ports, outdated software, misconfigured settings, or exposed services. Automated tools like network scanners and vulnerability assessment tools are commonly used in this phase. The results of these scans give testers a map of the system’s potential entry points, allowing them to focus on areas that might be more easily exploited. Scanning is a crucial step that bridges the gap between information gathering and active testing, providing the data needed to move forward with exploitation. - Exploitation
During the exploitation phase, testers actively attempt to breach the system using the vulnerabilities they identified in previous stages. The goal is to mimic real-world attacks, using methods such as SQL injections, privilege escalation, and password cracking to gain unauthorized access to sensitive systems or data. This phase helps determine how much damage an attacker could cause if they exploited the vulnerabilities, whether they could gain access to sensitive information, escalate their privileges, or disrupt operations. Successful exploitation gives the organization a clear understanding of its vulnerabilities’ real-world consequences and the potential risks they face. - Maintaining Access
Once testers have successfully exploited a vulnerability and gained access to the system, the next step is to attempt to maintain that access and escalate privileges. This phase simulates how an attacker would try to remain undetected while deepening their control over the compromised system. Techniques like installing backdoors, creating unauthorized user accounts, or hiding malicious scripts are used to retain access. Additionally, testers try to escalate privileges, moving from basic user accounts to administrator-level access. This phase is critical for understanding how long an attacker could potentially stay in the system, how much control they could gain, and how difficult it would be to detect their presence. - Post-Exploitation/Analysis
After maintaining access and attempting privilege escalation, testers move into the post-exploitation phase. Here, they assess the full extent and impact of the breach. The goal is to analyze how much data or control the attackers could have gained if the vulnerabilities were exploited in a real-world attack. This phase also involves determining the potential impact on the organization’s operations, reputation, and security posture. Post-exploitation analysis helps prioritize vulnerabilities by understanding their severity and potential damage, giving organizations a clear idea of which risks need immediate attention. - Reporting
The final phase of the pentesting process is reporting, where testers compile all their findings into a comprehensive document. This report typically includes details on the vulnerabilities identified, how they were exploited, the potential impact of each issue, and recommendations for remediation. The report is a key deliverable, offering actionable insights for the organization’s IT and security teams to address the vulnerabilities. Clear, concise, and actionable reporting is critical for ensuring that vulnerabilities are effectively mitigated and that the organization improves its security posture based on the findings of the test.
Aftermath of Pentesting: What Happens Next?
After a penetration test is completed, organizations should take the following steps:
- Reporting: The pentest results are compiled into a detailed report, outlining the vulnerabilities discovered and their potential impact. The security team then needs to go through this report to review the findings and prioritize vulnerabilities based on their severity, potential impact, and the business context.
- Remediation: Implement measures to address the identified vulnerabilities.
- Retesting: After the vulnerabilities are addressed, retesting should be performed to ensure the fixes are effective and no new issues have emerged.
- Continuous Improvement: The lessons learned from each pentest help organizations improve their defenses, enhancing their ability to prevent future attacks and make ongoing improvements to their security posture.
Common Challenges for Penetration Testing Management
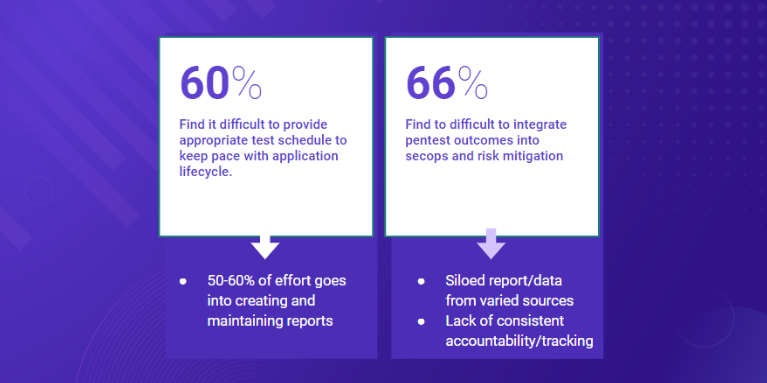
Many of the challenges organizations face with penetration testing are not tied to the actual testing itself but stem from difficulty managing resources and generating reports. Pentesting demand often exceeds capacity, and the biggest bottleneck is reporting. Highly skilled testers spend a significant amount of their time—sometimes up to 60%—reporting rather than testing. This severely limits testing capacity and strains resources, requiring either more time or more testers to meet demand.
Faster development cycles also exacerbate these issues. Research into organizations’ penetration testing performance found that 60% struggle to conduct penetration tests at the pace of development and 66% find penetration test findings difficult to operationalize into security processes.
This mismatch between development velocity and testing, reporting, and remediation efficiency creates challenges that can require more time, more people, and more costs to manage penetration tests and findings.
Manage Pentesting Effectively with ArmorCode
ArmorCode’s Penetration Testing Management Module reduces the time, effort, and cost of managing penetration tests and remediate risks by streamlining the complete penetration testing workflow.
The Penetration Testing Management Module simplifies the management of projects, creation of findings, report generation, and tracking of findings within ArmorCode.
Key features of the module include:
- An intuitive user interface: Simplify project management and finding creation.
- AI-powered ingestion: Automate data ingestion and analysis from multiple sources.
- A drag-and-drop report builder: Create customized reports with ease.
- Native ArmorCode integration: Get a unified view of all the findings from penetration tests, threat modeling, and other manual assessments alongside code, cloud, and infrastructure scanners.
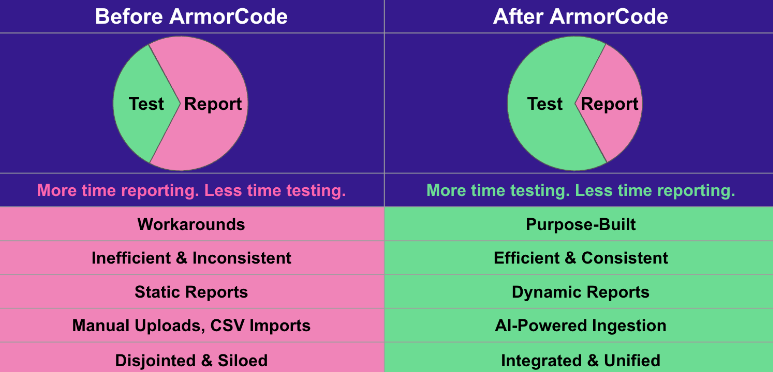
The pentest management module extends ArmorCode’s platform by unifying pentesting findings with those from code, cloud, and infrastructure scanners. This comprehensive solution enables organizations to effectively manage pentesting projects, create and prioritize findings, generate reports, and remediate vulnerabilities.
3 Mandatory Steps to Mature your AppSec Program Today
Read this whitepaper to discover how to mature beyond scanning and burn down your critical security debt by >80%.


