Cloud Security Posture Management (CSPM) Best Practices

Cloud Security Posture Management (CSPM) refers to a set of tools and practices to ensure the security and compliance of cloud resources and workloads. CSPM tools help organizations identify and remediate cloud security misconfigurations, monitor compliance with security policies, and maintain a strong security posture in cloud environments.
CSPM best practices are necessary to proactively manage security risks, comply with regulations, and ensure the integrity, confidentiality, and availability of data and resources in cloud environments. They contribute to a more resilient and secure cloud infrastructure while reducing the likelihood of security incidents. But while buying a CSPM tool is one thing, ensuring that you’re using it correctly is another. Let’s take a look at ten CSPM best practices to get the most out of your CSPM efforts.
Ten Important CSPM Best Practices to Follow
1. Protecting Against Common Misconfigurations
- Establish robust configuration management protocols to monitor and document alterations made to your cloud-based assets.
- Maintain a version history of configurations to revert to a known secure state if needed.
- Employ tools to automatically and proactively detect and resolve such problems.
- Enable comprehensive audit logging for configuration changes.
- Implement a systematic remediation process, this might involve rolling back changes, adjusting configurations, or applying patches.
2. Defining Security Policies & Standards
- Security policies and standards provide guidelines and rules that help ensure cloud resources’ secure design, deployment, and management.
- Identify organizational security objectives with precision, and forge all-encompassing security policies in alignment with these objectives.
- Policies should cover areas such as access controls, data encryption, network segmentation, and compliance requirements.
- Address how monitoring and auditing should be conducted. Specify which logs should be collected, how often they should be reviewed, and what actions should be taken based on the findings.
- Clearly state the consequences of policy violations.
3. Implement Automation & Orchestration
- Choose automation tools that are well-suited for CSPM in your specific cloud environment. Evaluate tools based on their features, compatibility with your cloud providers, and ease of integration.
- Clearly define your automation objectives and desired outcomes, and map your organization’s security policies, compliance requirements, and best practices to automation rules and configurations.
- Test automation scripts and actions in a controlled environment before deploying them in production.
- Regularly review automated actions and responses to ensure they align with the organization’s goals and do not introduce risks.
- Have backup plans and rollback strategies in place in case automated responses have unintended consequences.
4. Protecting Against Internal Breaches
- Implement strict RBAC policies that grant employees access only to the resources and data necessary for their roles
- Enforce MFA for accessing critical resources and encrypting data both at rest and in transit.
- Implement separation of duties to ensure that no single individual has unchecked control over critical operations
- Provide ongoing security training to employees to raise awareness about insider threats and encourage a security-conscious mindset.
- Have well-defined exit procedures to revoke access immediately when employees leave the organization or change roles.
5. Remediating Found Issues
- Utilize automation tools and scripts to remediate identified security issues. Automation helps ensure consistency and reduces human error.
- Prioritize remediation based on risk severity. Focus on critical vulnerabilities and misconfigurations that pose the highest threat to your environment.
- Classify issues as high, medium, or low severity to allocate resources effectively.
- Foster collaboration between security, DevOps, and other relevant teams. Establish clear communication channels for reporting, triaging, and resolving issues.
- Regularly update your CSPM tools and libraries to ensure they are capable of identifying and addressing emerging threats and vulnerabilities.
6. Discover & Inventory Assets
- Maintain an up-to-date inventory of all assets in your cloud environment.
- Regularly scan and discover new assets to ensure comprehensive coverage.
- Ensure that your asset discovery process covers all types of cloud resources, including virtual machines, containers, serverless functions, storage buckets, databases, and more.
- Implement a tagging and labeling strategy for cloud resources. Use tags to categorize assets by purpose, owner, environment, and other relevant attributes.
- Maintain an audit trail of changes to the asset inventory. This history can be valuable for tracking changes and investigating security incidents.
7. Choosing the Right CSPM Tool
- Evaluate the tool’s ability to perform a wide range of security checks, including configuration vulnerabilities, compliance violations, identity and access management issues, network security, and more.
- Look for tools that provide actionable insights and ideally be able to automatically apply fixes for common misconfiguration.
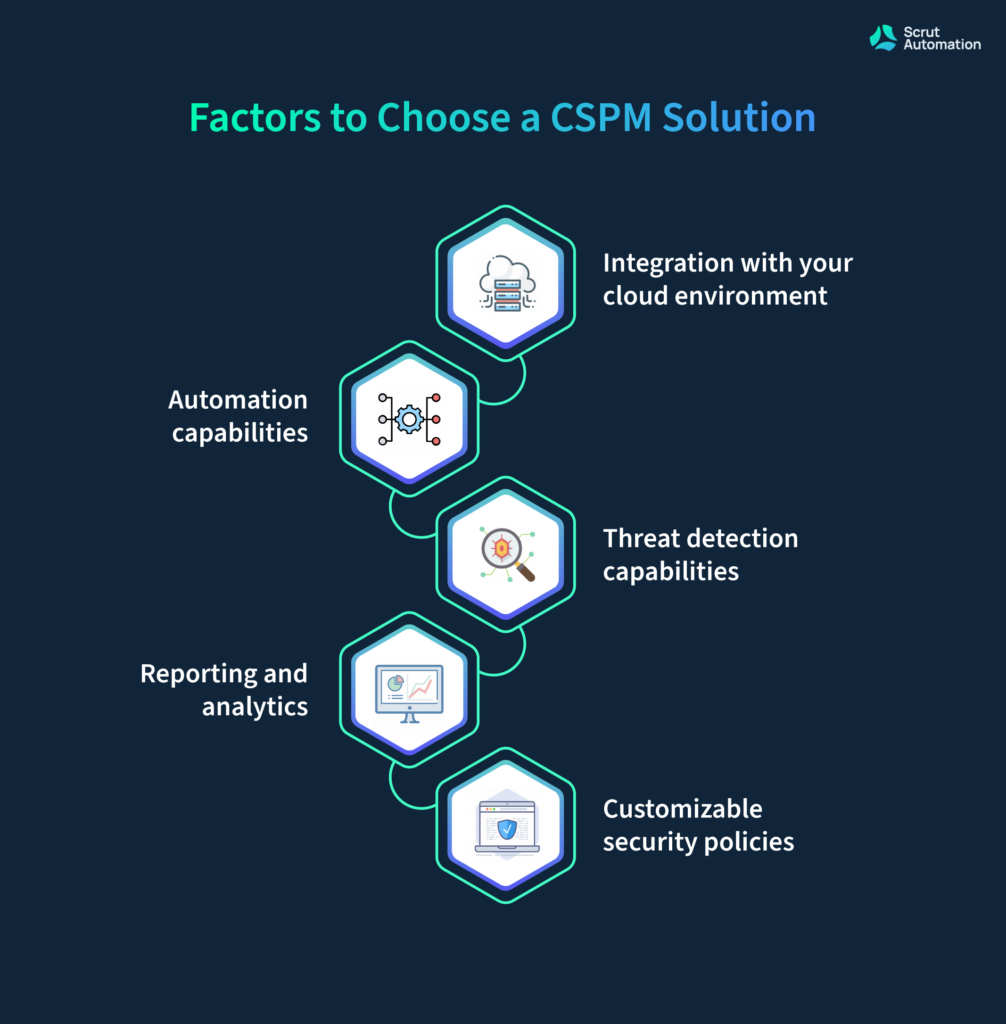
- Choose a tool that allows you to create custom rules and policies to match your organization’s specific security requirements.
- Research the reputation and track record of the CSPM tool vendor. Check for available customer support options, documentation, and community resources.
- Whenever possible, conduct trials or PoCs to evaluate the tool’s effectiveness in your specific environment before making a final decision.
8. Discovering Misuse & Compliance Violations
- Leverage predefined compliance templates provided by your CSPM tool or industry standards like CIS benchmarks and GDPR.
- Tailor CSPM policies to address specific industry regulations your organization must comply with.
- Implement continuous scanning of your cloud environment for compliance violations and security misconfiguration.
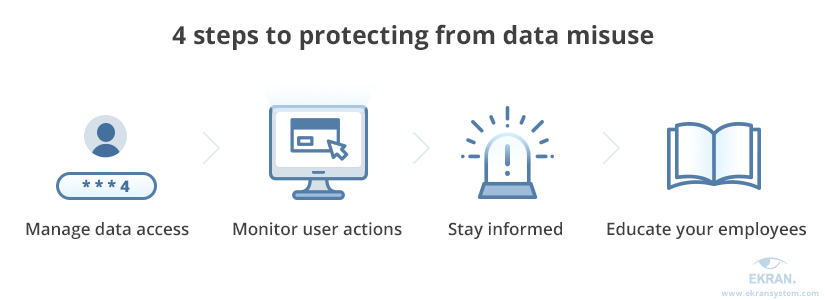
- Conduct routine audits to ensure that access rights are consistent with applicable data protection laws and that permissions match employee roles.
- Develop incident response plans specifically tailored to compliance violations or misuse. Define steps to take in case a compliance violation is detected.
9. Using Secure Coding Standards
- Choose widely recognized and established secure coding standards such as OWASP Top Ten, CERT Secure Coding, and CWE/SANS Top 25.
- Integrate security practices into the software development lifecycle (SDLC) from the very beginning.
- Incorporate security reviews, threat modeling, and code analysis into each development phase.
- Avoid exposing detailed error messages to end-users, as they can reveal valuable information to attackers.
- Develop and maintain internal secure coding guidelines and documentation that developers can reference.
10. Manage Updates & Patches
- Set up a testing environment to evaluate the impact of patches on applications and systems before deploying them in production.
- Implement a regular patching schedule to ensure that systems are up-to-date with the latest security updates.

- Implement network segmentation to isolate critical assets from potentially vulnerable systems. This limits the spread of vulnerabilities and reduces the attack surface.
- Document the patch management process, including roles and responsibilities, testing procedures, and deployment steps.
- Ensure that newly deployed resources are promptly patched before they become vulnerable.
Leading CSPM Tools for Strengthening Cloud Security
The CSPM market is ever-evolving, and deciding what’s best for your environment will change. ArmorCode is committed to integrating with top CSPM tools from your vendor of choice to ensure that you can unify your cloud scanning with AppSec and infrastructure vulnerability management. Teams use ArmorCode to unify, prioritize, and remediate security issues across their entire ecosystem.
Some great CSPM tools that ArmorCode integrates with include:
- AWS Security Hub
- Aqua
- Cloud Optix
- Lacework
- Orca Security
- Prisma Cloud Redlock
- Sonrai Security
- Sysdig
- Wiz



