Burn Down Your Vulnerability Backlog with Asset-Centric Workflows

Vulnerability management is no longer just about identifying weaknesses; it’s about prioritizing and acting on the highest risks before they become critical issues. Many organizations, however, struggle with legacy programs that generate a flood of data without actionable insights, leaving vulnerability management teams overwhelmed, reactive, and stretched thin.
Infrastructure and cloud security scanners are great at identifying vulnerabilities. However, there are far too many infrastructure assets and corresponding vulnerabilities that vulnerability management teams must prioritize and remediate for their current vulnerability management programs to handle. Many vulnerability management programs don’t incorporate application vulnerabilities either.
The traditional CVSS-centric approach to prioritization doesn’t reduce the volume enough and leads to missing lower severity vulnerabilities that impact your specific business more seriously. Beyond prioritization, there are significant challenges when it comes to determining asset owners and implementing ticketing workflows, leading to slow, manual remediation efforts.
Vulnerability management teams are facing a reality where they’ve solved the problem of not having visibility into vulnerabilities in the environment, and are now faced with a problem of too much data. They want to bring everything together to get one risk score they can trust, one prioritized backlog of vulnerabilities, and so on. Amidst these struggles, the demand for a more strategic solution, Risk-Based Vulnerability Management (RBVM), has grown. Enterprises now seek a solution that provides unified visibility across cloud, infrastructure, and/or applications, prioritizes vulnerabilities based on actual risk, streamlines remediation, and empowers vulnerability management teams to respond swiftly to the most pressing threats.
Leveraging asset-centric workflows to implement risk-based vulnerability management
One of the key use cases that teams leverage in the AI-powered ArmorCode Platform is RBVM. I wanted to take a moment to highlight an aspect of the ArmorCode Platform that powers RBVM for vulnerability management teams: asset-centric workflows.
Asset-centric workflows make infrastructure assets a first-class citizen within the ArmorCode Platform, empowering vulnerability management teams with a clearer, more accurate view of their assets than ever before, and enabling them to focus their vulnerability management efforts on the highest risk assets.
This feature makes it possible to develop a new asset inventory or enrich an existing one from known asset inventories and new Findings. It delivers an unprecedented, cohesive view of an organization’s infrastructure and cloud assets, helping security teams stay on top of the evolving asset landscape.
Beyond just visibility, ArmorCode enhances asset ownership information by associating each asset with the right owners when available and flagging gaps in ownership details, especially for assets identified in Findings. This asset-centric approach empowers teams to prioritize vulnerabilities with full context on asset impact and ownership, creating more targeted and efficient remediation workflows that center around assets, not just findings.
ArmorCode unifies application security and vulnerability management teams into one platform, fostering collaboration, and shared visibility, enabling organizations to reduce exposure and risk overall. With assets as a foundational element, security teams can leverage ArmorCode’s full potential to manage and remediate vulnerabilities across their infrastructure, cloud, and applications with clarity, precision, and confidence.
Create a single source of truth for your assets
Asset ownership is a complex issue to solve. Unlike code repositories, infrastructure assets have no clear ownership inherent to them. This often leaves vulnerability management teams at a loss to determine who to go to when they do uncover vulnerabilities.
While many enterprises have an asset inventory in a specific tool (e.g., ServiceNow, Axonius, RunZero), this inventory is frequently incomplete. Assets are managed across multiple systems that are not all owned by the IT team. Additionally, developers are spinning up ephemeral assets (e.g., containers) as part of their workflows and scanners always seem to find new assets that aren’t in the inventory. As a result, teams struggle with assets that exist and are not being scanned and assets that are being scanned but don’t exist in the inventory. This leads to a gap in asset inventory. Mid-sized companies often face even greater challenges, sometimes lacking a formal asset inventory altogether.
By integrating known asset inventories and correlating this data with asset information gleaned from Findings, ArmorCode helps identify gaps in existing inventories. Through this correlation, ArmorCode extends ownership information into Findings, and highlights where ownership info is missing if an asset is discovered from a Finding. With asset-centric visibility, ArmorCode consolidates assets discovered from Findings with the main inventory, making it possible to develop a new asset inventory or update an existing one.
Vulnerability management teams also gain insight into assets that are in their inventory but not appearing in any scans, helping them understand where they may be missing coverage for their security scanners. This helps them with the most complete, accurate, and up-to-date understanding of their infrastructure assets.
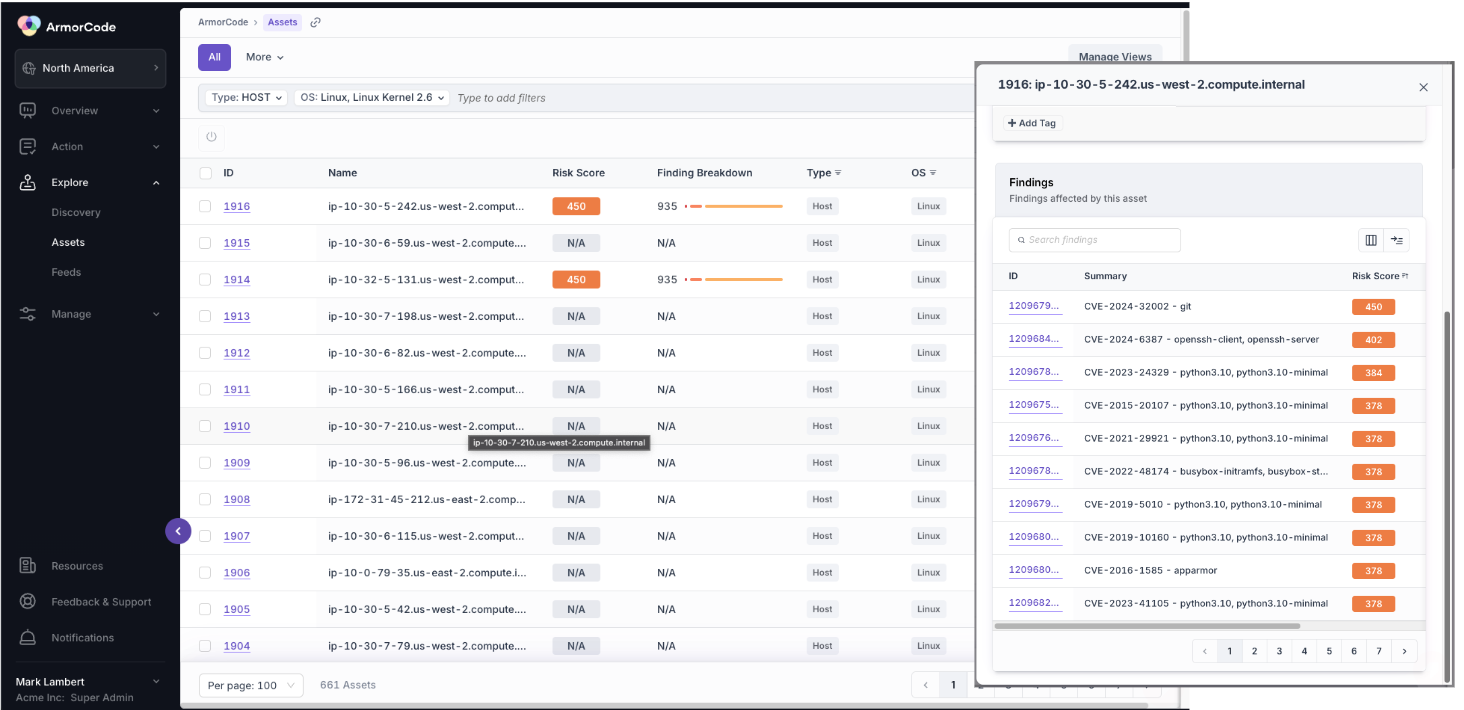
Prioritize risk based on underlying assets to remediate large chunks of vulnerabilities with a single patch
With ArmorCode’s asset-centric approach, vulnerability management teams can prioritize risks by leveraging enhanced asset metadata, such as criticality, ownership, and categorization. This deeper level of asset insight allows vulnerability management teams to tailor vulnerability remediation based on the asset’s importance, helping to streamline efforts by focusing on high-risk areas that impact critical assets.
By treating assets as first-class citizens in ArmorCode, vulnerability management teams can create remediation workflows centered around assets rather than isolated Findings, which enables a more holistic approach to addressing multiple vulnerabilities at once.
For instance, let’s say a vulnerability is discovered in a widely used web server component across multiple applications in an organization. ArmorCode’s asset-centric workflows allow vulnerability management teams to group all Findings by this shared asset and identify it as a high-priority asset. Now, rather than creating a large number of individual tickets for each vulnerability, the team can create a single ticket to apply a single patch to the shared web server component, greatly reducing the number of tickets sent to the IT teams and making a large impact on the vulnerability backlog in one fell swoop.
This approach not only accelerates the remediation process but also frees up valuable resources, allowing teams to focus on other critical security tasks. By correlating and prioritizing vulnerabilities with this asset-based lens, ArmorCode empowers organizations to maximize remediation efficiency, ultimately reducing their risk profile with less manual effort.
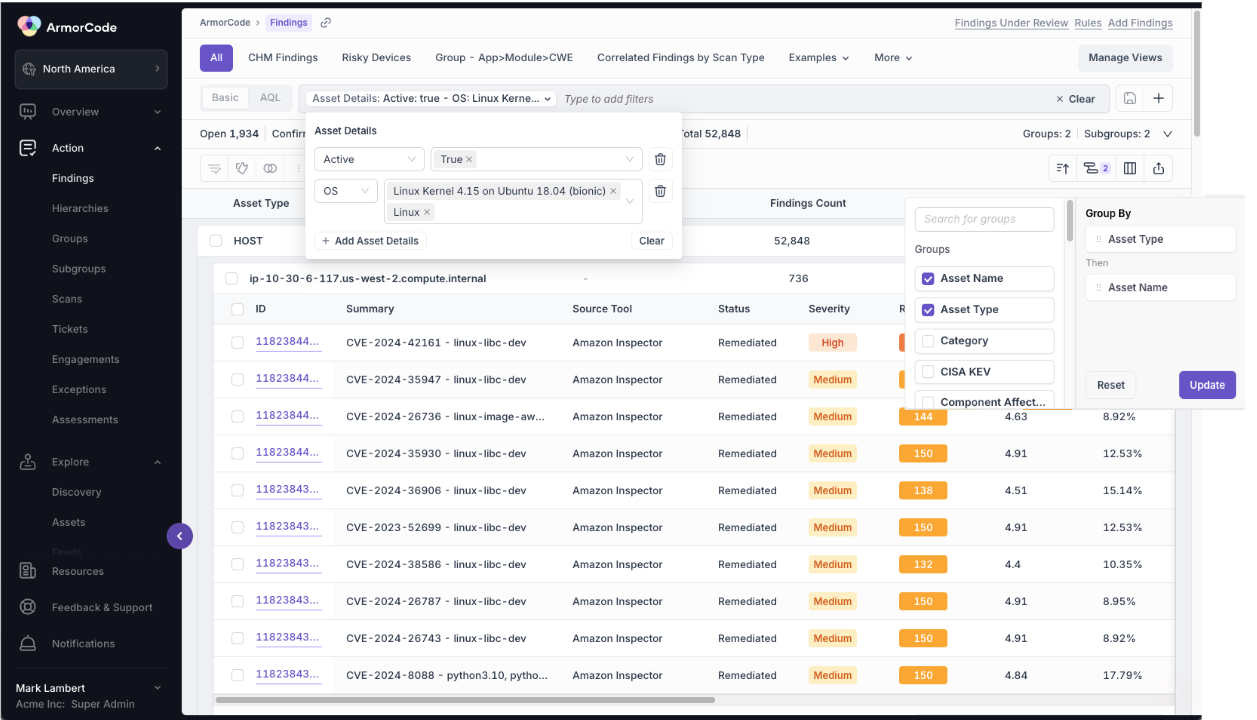
Burn down your vulnerability backlog
A fact of life is that vulnerabilities pile up faster than teams can remediate them. The work most vulnerability management teams are focused on is not fixing every issue, but rather figuring out how to focus on the smaller percentage of vulnerabilities that matter most to their business, and burning those down.
ArmorCode’s asset-centric workflows help vulnerability management teams burn down their vulnerability backlog by providing clear visibility into asset ownership, enabling security teams to automate remediation workflows and prioritize high-impact patches effectively. When combined with the ability to see which assets would make the greatest impact to the backlog with a single patch, vulnerability management teams can both accurately prioritize and remediate what matters quickly. With each asset’s owner readily visible in the ArmorCode platform, security teams can automatically route vulnerability management tasks to the correct stakeholders, drastically reducing the time it takes to track, assign, and remediate issues.
Automated workflows allow security teams to triage vulnerabilities faster, sending critical context directly to asset owners for immediate action. For example, rather than generating separate tickets for each affected system, ArmorCode consolidates vulnerabilities tied to the same asset group, enabling a single, efficient ticket that covers multiple issues at once. This approach not only accelerates patching but also eliminates redundant tasks and ticket submissions, cutting down on the administrative overhead that clogs up vulnerability backlogs.
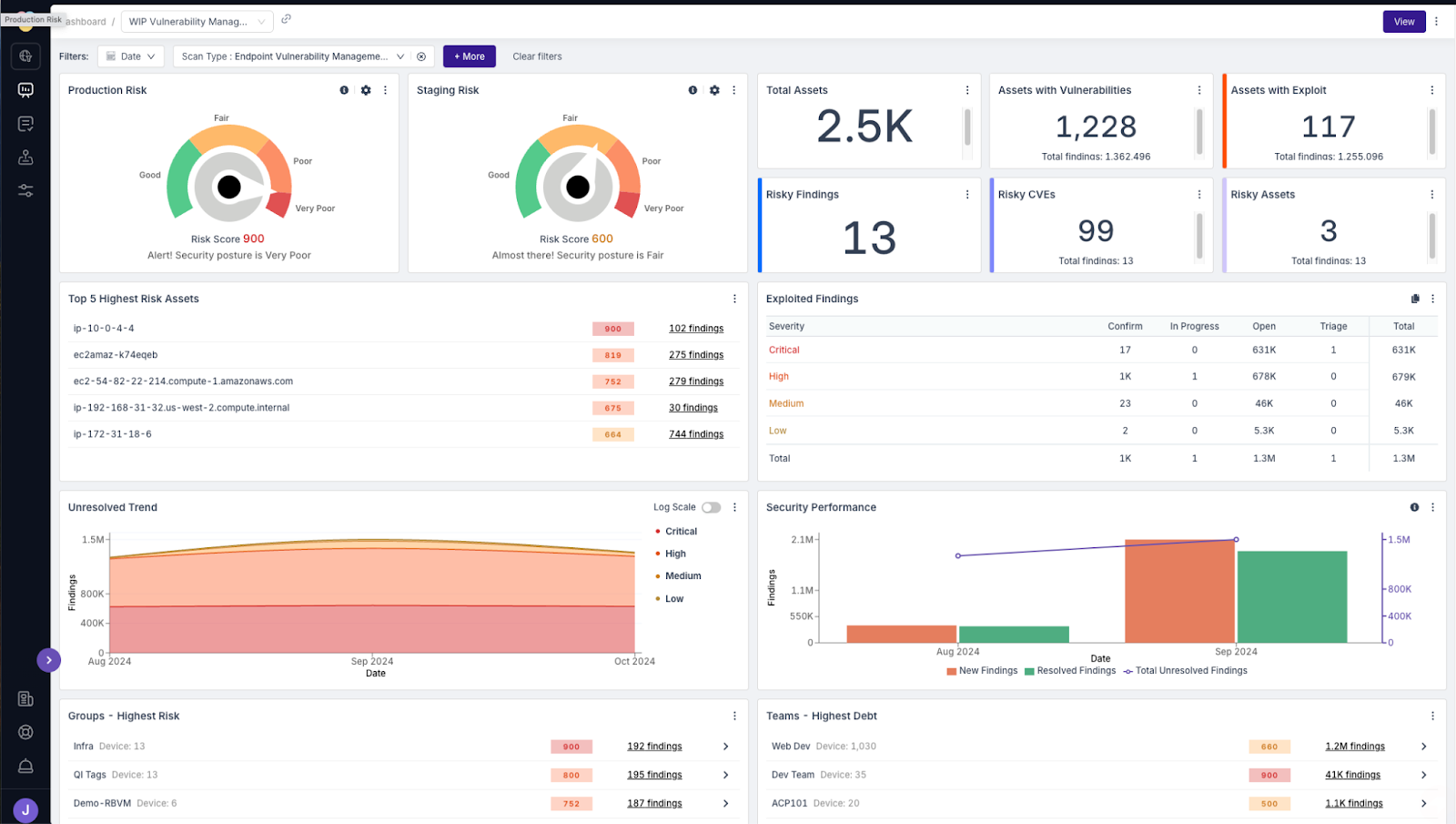
Power your vulnerability management program with asset-centric workflows
RBVM in ArmorCode enables vulnerability management teams to unify their vulnerability management across their ecosystem and focus on the risks that matter most. Asset-centric workflows is one part of the RBVM solution that helps teams address the challenges of incomplete and missing assets within an organization’s asset inventory. The ArmorCode Platform pinpoints where ownership details are lacking for assets identified through Findings, giving vulnerability management teams more comprehensive and accurate asset information.
ArmorCode delivers an AI-powered platform for vulnerability management teams to address risk by unifying, prioritizing, and remediating vulnerabilities across infrastructure, cloud, containers, and applications.
Normalize and triage findings across your entire enterprise based on actual risk to your business, and automate remediation workflows to burn down vulnerabilities faster than ever before. No matter where your scanners uncover vulnerabilities, ArmorCode empowers your team to implement a consistent, independent process for triage and remediation. Now they can find and fix what matters most, identify asset owners, and reduce MTTR across the entire vulnerability management lifecycle.
Schedule a personalized demo to learn more about ArmorCode and Risk-Based Vulnerability Management.



