Streamline Software Supply Chain Security with ArmorCode & Endor Labs

Organizations must address software supply chain security as part of a comprehensive security program. As software development increasingly relies on third-party components and supply chains become more interconnected, it is critical organizations identify and prioritize risks from open-source and third-party vulnerabilities, ensure the integrity of CI/CD pipelines against sophisticated attacks, and provide visibility into software components via software bill of materials (SBOM). However, this adds further layers of complexity that teams must manage.
Integrating Endor Labs’ Software Supply Chain Security solution into ArmorCode’s leading Application Security Posture Management (ASPM) platform empowers customers to simplify and streamline software supply chain security as part of a comprehensive and risk-based application security program. The partnership provides a holistic approach for organizations to identify, prioritize, and address supply chain risks without slowing development velocity or taxing productivity.
This blog post explores the challenges and complexities of securing software supply chains and how synergies between Endor Labs and ArmorCode empower customers to manage and reduce risk at speed and scale.
Securing the Software Supply Chain
The software supply chain is a prime target for cyber attackers and poses a complex security challenge. Vulnerabilities in open-source libraries can proliferate to affect thousands of applications, and targeted supply chain attacks like the SolarWinds example demonstrate how infiltrating a single point within the supply chain can compromise multiple downstream organizations making these attacks highly efficient and impactful.
However, the complex nature of modern software development makes it challenging to gain clear visibility into supply chain risks spread across upstream dependencies, CI/CD build pipelines, and downstream applications. For example, using an open-source library with a known vulnerability does not inherently mean those vulnerabilities are exploitable in a given application. Conversely, an open-source library that seems secure today may contain latent vulnerabilities that could lead to exposure tomorrow.
Amid this challenge, organizations must appropriately balance remediation efforts and security posture with development velocity. Cumbersome security processes and wasted effort hinder development, while insufficient security exposes organizations and end users to costly attacks. Endor Labs’ holistic approach builds resilience against sophisticated cyber threats without taxing productivity by implementing these core tenants across the SDLC:
Select Better Open Source Software
Select better open source dependencies with 150+ checks and scoring based on security, legal, popularity, activity, and quality. Defend against OWASP OSS Top 10 Risks [LINK] such as typosquatting, malicious and abandoned dependencies.
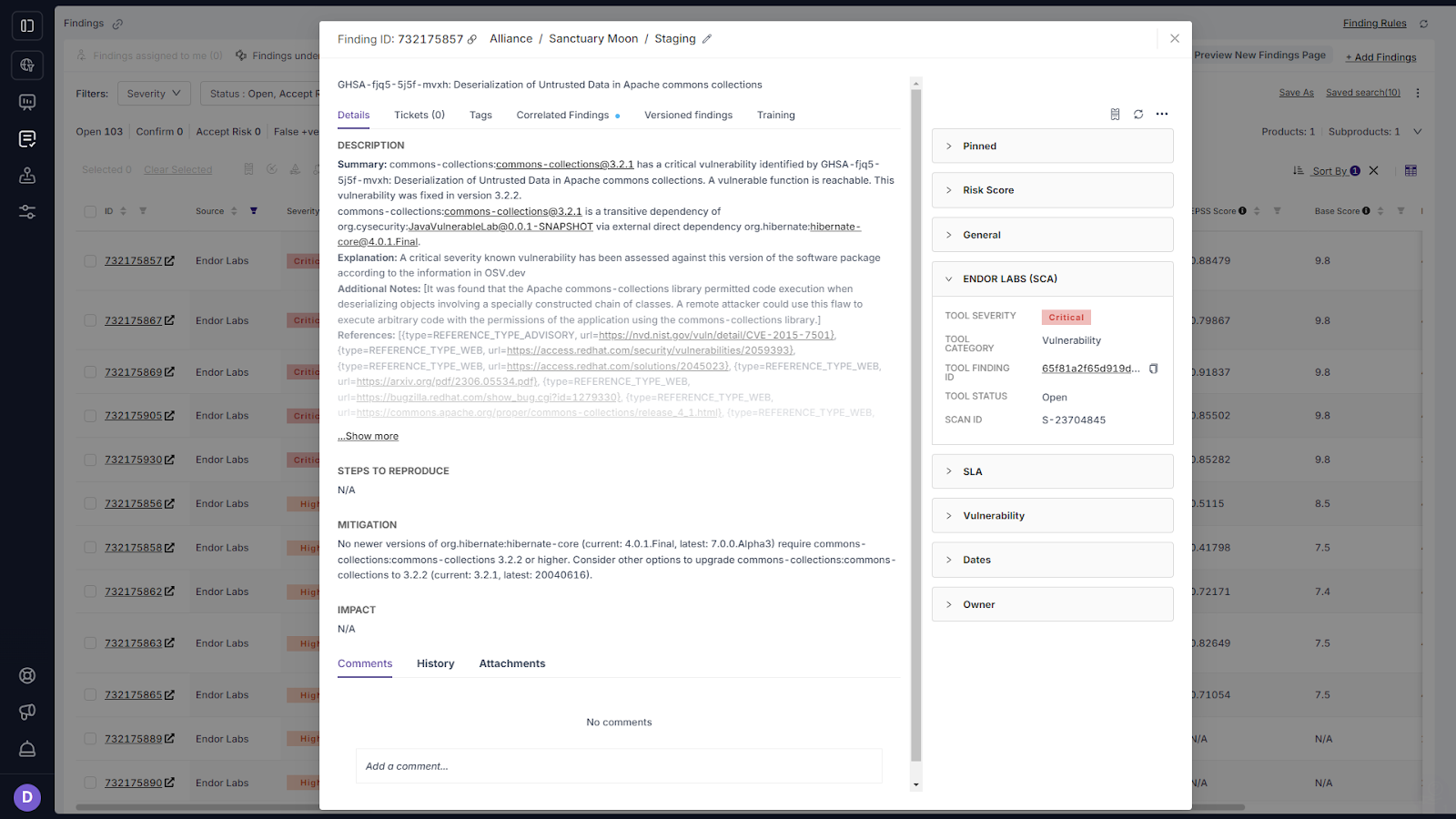
Prioritize Open Source Vulnerabilities (SCA)
Cut over 90% of vulnerability noise with function-level reachability analysis across both direct and transitive dependencies. Codify highly customizable policies to provide developers feedback in PR comments, break builds in CI, or simplify notify them via Jira tickets.
Secure Repositories and CI/CD Pipelines
Gain visibility into security tool coverage across your CI/CD pipelines and continuously monitor the security posture of source code repositories. Detect repo and GitHub Actions misconfigurations, best practices, and risks with over 50 out-of-the-box policies, including coverage for CIS best practices for GitHub.
Trust What You Ship with Artifact Signing
Ensure the authenticity of software artifacts with a single GitHub action. Artifact signing is a hassle-free alternative to Sigstore that confirms code provenance and lack of tampering. Cryptographic artifact signatures are a powerful tool to enable strong admission control and traceability to support effective security, quality, and compliance programs.
Ensure compliance across the SDLC
Detect legal and licensing risk, and centrally create, manage, and analyze SBOM & VEX. Prioritize applicable vulnerabilities for PCI-DSS and FedRamp and accelerate compliance with CIS, NIST, SSDF, SLSA, EO 14028, and more.
The capabilities above highlight the need for dedicated solutions that cater to the specialized requirements of software supply chain security. However, the supply chain is only one of many threats facing an expanding attack surface. ArmorCode complements Endor Labs by unifying all security data inclusive of supply chain findings to manage application risk holistically.
Managing Software Supply Chain Security as Part of ASPM with ArmorCode
ArmorCode’s ASPM platform solves the challenges and complexities of managing software supply chain security as part of a complete application risk management program. Integrating Endor Labs with ArmorCode AI-powered ASPM platform allows seamless management, prioritization, and remediation of supply chain risks
Together, the two solutions provide visibility into supply chain risk and enable teams to:
Simplify and streamline software supply chain security
The integration simplifies and streamlines software supply chain security by providing a single platform for managing both application security posture and software supply chain risks.
Improve software supply chain risk prioritization
With Endor Labs’s data integrated into ArmorCode’s solution, organizations can enhance their risk prioritization and automate remediation processes, addressing the highest-risk vulnerabilities first and improving overall security posture.
Elevate the efficiency and effectiveness of software supply chain remediation efforts
The combined solution improves the efficiency and effectiveness of remediation efforts by streamlining and automating security workflows from data ingestion and risk assessment to triaging, ticketing, and tracking.
Getting Started with the ArmorCode and Endor Labs
Integrating Endor Labs into ArmorCode’s ASPM platform is straightforward thanks to an out-of-the-box integration. To get started:
- Generate an API Key with read-only permission in Endor Labs
- Navigate to Security Tools in the ArmorCode Platform
- Select Endor Labs
- Add a Configuration with your Endor Labs API credentials
- Map Endor Labs projects to ArmorCode
Software supply chain security is a critical aspect of application risk management. By leveraging the strengths of ArmorCode and Endor Labs, organizations can simplify and streamline software supply chain security, enhance risk prioritization, and improve the efficiency and effectiveness of remediation efforts.
Explore the ArmorCode and Endor Labs integration today. Schedule a personalized demo to learn more.



